ASA 5512 ACL 无效 分析案例:
内网 gi 0/0 192.168.60.2
公网 gi 0/5 xxx.xxx.xxx.xxx
ASA 5512 9.1
需求:
将公网 xxx.xxx.xxx.xxx:3389 映射到内网 192.168.60.2:3389
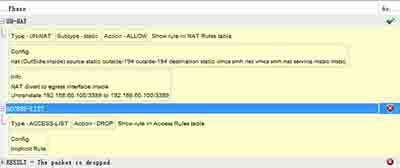
通过package-trace工具测试的结果如下:
请见截图
日志显示如下:
Deny IP spoof from (42.62.95.194) to 192.168.60.100 on interface OutSide
问题:
1.根据日志及测试工具结果,判断是被ACL deny了,但是为什么呢?因为我的ACL配置有错误吗?还是因为我的ACL没有生效?
2.我在公网PC上 telnet 防火墙80端口,则会出现请求被deny的日志,这是没问题。而我telnet 3389或其他端口,FW日志没有任何显示,就貌似没有请求过来,这是为什么呢?
ASA Version 9.1(2)
!
hostname ciscoasa
domain-name smh.net
enable password pLSOnxkiiRfoCrRc encrypted
names
ip local pool VPN 192.168.60.240-192.168.60.250 mask 255.255.255.0
!
interface GigabitEthernet0/0
nameif inside
security-level 90
ip address 192.168.60.2 255.255.255.0
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
nameif OutSide
security-level 100
ip address 42.62.95.194 255.255.255.240
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa912-smp-k8.bin
ftp mode passive
clock timezone CST 8
dns domain-lookup inside
dns domain-lookup OutSide
dns server-group DefaultDNS
name-server 211.98.2.4
domain-name smh.net
object service ssh_7722
service tcp source eq 7722 destination eq 7722
object network vmcs.smh.net
host 192.168.60.100
object service mstsc
service tcp source eq 3389 destination eq 3389
object network outside-194
host 42.62.95.194
object network In
object service http
service tcp source eq www destination eq www
object network outside-195
host 42.62.95.195
object network inside-network
subnet 192.168.60.0 255.255.255.0
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group-search access-control
access-list OutSide_access_in extended permit object mstsc any any log debugging
access-list inside_access_in extended permit object mstsc any any log debugging
access-list inside_access_in extended permit object-group TCPUDP object vmcs.smh.net any eq domain
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu OutSide 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-713.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (OutSide,inside) source static outside-194 outside-194 destination static vmcs.smh.net vmcs.smh.net
service mstsc mstsc
access-group inside_access_in in interface inside
access-group OutSide_access_in in interface OutSide
route OutSide 0.0.0.0 0.0.0.0 42.62.95.193 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication telnet console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http 0.0.0.0 0.0.0.0 inside
http 0.0.0.0 0.0.0.0 OutSide
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map OutSide_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map OutSide_map interface OutSide
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable OutSide client-services port 443
telnet 0.0.0.0 0.0.0.0 inside
telnet 0.0.0.0 0.0.0.0 OutSide
telnet timeout 30
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp authenticate
ntp server 210.72.145.44 source OutSide prefer
ssl encryption rc4-sha1 aes128-sha1 aes256-sha1 3des-sha1
webvpn
username duckling password znZCFn3Zzd6Pbj5F encrypted privilege 15
username admin password a54LRNMRW6ia5dEY encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:efeb349e2b0ee6b4095dd2ac1346e87b
: end
ciscoasa#
解答:object service mstsc
service tcp source eq 3389 destination eq 3389
这个是不对的。源端口是随机的,需要改一下。
object service mstsc
service tcp destination eq 3389
access-list OutSide_access_in permit object mstsc any host 192.168.60.2
或者直接
object net host-3389
host 192.168.60.2
nat (inside,outside) static inter service tcp 3389 3389
access-list outside-3389 permit tcp any host 192.168.60.2 eq 3389
access-group outside-3389 in int outside
- 北京机房搬迁改造公司,系统集成有哪些公司?-2019-11-04
- 如何打造一个安全的网络环境?政府要做到这四点-2019-11-04
- 北京办公室网络布线,综合布线施工价格-2019-11-04
- 深信服产品专业上网行为管理,安全设备有保障-2019-11-04
- 两年内网络安全市场规模将达千亿级别?来看看详细分析-2019-11-04
- 北京炫亿时代专业机房设备除尘,机房网络改造-2019-11-04
- 企业如何保障移动办公的安全性?移动办公存在的七大安-2019-11-01
- 北京深信服AC-1000-A400产品租赁购买,专业IT上网行为管理-2019-11-01
- 互联网企业软件开发如何才能没有漏洞?专业工程师给出-2019-11-01
- 如何避免APP的“越权”行为?要靠制定相关法律法规-2019-11-01

 企业通讯
企业通讯
